Jun 05, 2020 Malwarebytes for Mac's free version is about as streamlined as an antivirus software can get. It will scan your system and remove Mac-based malware with really impressive consistency, but it won't do much else. The majority of Mac OS X users should know that starting with version 10.6.8, Apple has integrated a company-baked anti-malware tool which offers a first level of protection. Jun 30, 2017 Here we've gathered some of the best free and paid virus malware protection software for Mac OS X. But the question is do your Mac need a malware scanner. Yes, Mac devices also need Antivirus. However, compared to Windows. Mainly there are two reasons which make Mac OS X device more secure compared to Windows. Because MacOS is an Unix-based. Jul 04, 2012 The only malware in the wild that can affect Mac OS X is a handful of trojans, which can be easily avoided by practicing safe computing (see below). Also, Mac OS X Snow Leopard and Lion have anti-malware protection built in, further reducing the need for 3rd party antivirus apps.
Effective Guide To Delete OpticalUpdater from Mac System
OpticalUpdater is an unwanted program that mostly spread via Fake Adobe Flash player update. It is mainly designed to promote fake search engine by the modifying browser setting and delivers intrusive advertisements. It has tendency as a web browser hijacker and adware program. It also designed to collect users browsing activities. Most of the users download or install System Software unintentionally so that it is classified as a potentially Unwanted program (PUAs).
The main aim of this Browser hijacker is to hijack all popular and mostly used web browsers like as Mozilla Firefox, Internet Explorer, Google Chrome, Safari, Edge and others. It makes the browser so strange by the several alternations like as homepage, search engine and DNS setting. Due to the changes of DNS setting users are unable to search any site as usual. It replaces the homepage and default search engine with fake searching site URL. So that while users search any query on it, open new tab and paste URL then they redirect to the sponsored site. It is common that fake search engine never get relevant search result so they redirect to Google, Yahoo, Bing and other genuine search engine and displayed results generated by them with some sponsored ads.
As an adware program OpticalUpdater delivers various kinds of annoying and intrusive advertisements including coupons, banners, discounts and other intrusive ads that looks very attractive at the first inspection. But malicious links or content hides into them. Once clicking on these intrusive adverts redirect to various questionable and malicious site and the installation of some potentially unwanted program. These ads are mainly designed to diminish the browsing experience by downpour surfing speed as well as covering the page content. Scammers behind these ads generate illegal revenue on pay per click technique. So we are highly advice do not click on such ads even accidentally.
More Harmful Effects Cause by OpticalUpdater:
It can corrupt your System files and Windows registries as well as create duplicate file as a similar name to regenerate itself after removal. It disables the System security and privacy by inactivate firewall, task manager, control panel and real antivirus program to makes the PC defenceless. It opens back doors to install other harmful infections like as malware, spyware, Trojan, Ransomware to makes the PC more damage quickly.
It has data tracking abilities, so it tracks users online browsing data like as search queries, web histories, cookies and pages viewed etc. It also monitors online keys habits to collect personal and confidential information like as email-id, password, bank account details, IP address, geo-locations etc. After that share such details to the Cyber offender for illegal use such as fake purchasing, fraudulent, transaction money and even identity theft. To protect your System privacy issues and financial losses, it is highly advice to remove OpticalUpdater as quickly as possible.
How did OpticalUpdater get inside into your PC:
OpticalUpdater commonly get inside into the System via the bundling method. Bundling is a deceptive marketing technique of packing regular software with unwanted and malicious additions. Most of the users download or install System software via third party download channels such as software.com, downloader.com and third party downloader site. They often skip custom, advance and other important settings. Skipping such setting cause the installation of potentially unwanted software.
How To Avoiding the installation of potentially Unwanted Program:
It is highly advice do not download and install System software from third party downloader site. Software must be downloading and install from official and trustworthy download channels. It is important to read the installation guide carefully till the end. Must select custom, advance and other important settings. Clicking on the malicious ads cause the infiltration of malicious infection. So do not click on them even accidentally. Must scan the PC with reputable antimalware tool regularly. Safari update mac 10 6 8. If your System is really infected with unwanted ads then we are highly advice to remove OpticalUpdater by using automatic removal tool.
Where is the alt key on a mac keyboard. Mac users can download and check if the free scanner can help cleaning OpticalUpdater from their infected system
Remove OpticalUpdater from Mac OS X system
We are going to discussion two possible ways to perform OpticalUpdater removal 1) Manual Removal and 2) Automatic Removal method. The Manual process is more suited to the people who know their system really well. This method is quite unreliable, takes lots of time and need technical skills. Any mistakes during the process can cause major damage to your system. If you cannot reverse such damages, use Automatic Removal Method. It is easy to detect and remove any malicious programs like OpticalUpdater from the device using some reputable antivirus tools like Combo Cleaner. Such tools also offer other important tools like duplicate files finder, clean junk files, huge file finder, privacy protection, browser cleaning and Mac speed booster. For the convenience, we are here providing you both the manual and automatic instruction one by one.
How to remove OpticalUpdater manually?
- First of all, open the Utilities folder on your Mac
- Search for the option Activity Monitor and double-click on it
- Select malicious or suspicious processes related to the OpticalUpdater and click on the cross button from the upper left side corner to end the task
- When a pop-up dialogue box appears on the screen, click on the Force Quit button
The OpticalUpdater can keep coming back on the device if the core files are not completely removed. We recommend you downloading Combo Cleaner. Using this, you can remove all the hidden files and also save time and effort as well.
Automatically remove OpticalUpdater from the Mac OS X
- Click on the link to download Combo Cleaner Antivirus on your Mac
- Drag the install file to Applications folder to install the program
- Go to Antivirus tab, Select Scan Mode and press Start Scan button
- Software will find all the files. You just click on the Remove all the threats button
Remove OpticalUpdater from Applications
- Click Go button at the top left of the screen and select Applications
- Wait till the Applications folder appears, and look for OpticalUpdater or other suspicious programs on it and then right click on each entry and select Move to Trash
Remove OpticalUpdater related files and folders
Click the Finder icon (from menu bar), choose Go and select Go to Folder
Step 1:Check the malware generated files in the Library/LaunchAgents folder
In the Go to folder…. bar, type /Library/LaunchAgents
Look for any recently added suspicious files in this folder. Such files could be 'installmac.AppRemoval.plist', 'myppes.download.plist', 'mykotlerino.ltvbit.plist', 'kuklorest.update.plist', etc. If you find any similar, move them to the Trash.
Step 2:Erase the suspicious files from '/Library/Application' Support folder
Type '/Library/Application Support' in this folder
In the Application Support folder, you may find MplayerX or NicePlayer or other similar suspicious folders. Move these folders to the Trash.
Step 3: Check the /Library/LaunchDaemons Folder for the suspicious files created by malware
In the Go to Folder… bar, type /Library/LaunchDaemons
In the LaunchDaemons folder, search for the files 'com.aoudad.net-preferences.plist', 'com.myppes.net-preferences.plist', 'com.kuklorest.net-preferences.plist', 'com.avickUpd.plist', etc and move them to the Trash
Step 4: Use Combo Cleaner and scan your Mac
After performing all the steps mentioned before in correct manner, your Mac should be cleaned of the infections. However, you must ensure this by running a scan to the power-station with Combo cleaner anti-virus.
After the download, double click the combocleaner.dmg installer in the opened Window drag and drop the antivirus tool icon on the top of the Application icon. Thereafter, open the Launchpad and press on Combo Cleaner icon. The Combo Cleaner then starts update its virus definition database – you should have to wait till the moment till the process is completed. Next thing you do is to click on the Start Combo Scan button.
The anti-malware tool starts scanning your Mac device for malware infections. After the scanning, if it displays no threats found – you can continue with the removal guide, otherwise you have to perform removal of the found infections.
After removing the files and folders generated by the malware, the next thing you do is to remove the rogue extensions installed on the Internet browsers.
Remove OpticalUpdater from Internet browsers
Instruction on removing suspicious Safari extensions:
Open Safari from the menu bar, select Safari and click preferences
In the preferences window, select extensions and search for recently installed suspicious extensions. If any such extensions located, click on uninstall button next to them.
Generally, users can simply remove all these extensions. However, if you have any problems with the browser redirects and the unwanted advertisements, we recommend you 'Reset the Safari'. The reset feature is capable of fixing various issues related to the browser hijackers and adware. Also, the resetting the browser does not mean that the essential information such as bookmarks and open tabs will also be deleted. By using the steps, you will reset the extensions, themes, search engines, security settings, plug-ins settings, toolbar customization, user styles and other settings. Here are the step by step instructions on performing the steps:

Open the Safari main menu and Choose Preferences from the drop down menu
Go to the Extension tab, and turn off the extension slider to disable all the installed extensions in the Safari browser.
Next step is to check the homepage. Go to the preferences option and choose General tab. Change the homepage option to the default one
If the search engine also got changed, you can set default or other web searcher according to your choice. For this, go to the preferences window and select the 'Search' tab and select the search engine provider that you want to
Next thing you need to do is to clear the browser Cache. For this, go to the preferences window and select the 'Advanced' tab and click on the show develop menu in the menu bar
Then, Select Empty Caches from the Develop menu
Thereafter, remove the website data and the browsing history. Go to Safari menu and select Clear History and Website Data. Choose all history and then click on Clear History.
Guides on removing malicious plug-ins from Mozilla Firefox:
Open the Mozilla Firefox, Click on the Menu at the right top corner of the screen. From the opened menu, choose Add-ons
Best Free Mac Malware Removal
Choose the Extension tab for the recently added suspicious add-ons, if located -click the Remove button next to them. You can safely uninstall all the extensions, however, if you find any trouble, we recommend you Reset the Mozilla Firefox.
- Open the Mozilla Firefox and click on the Firefox button (at the top left corner of the main window)
- In this menu, look for Help sub-menu and select Troubleshooting information
- In this information page, click on the Reset Firefox button
- On the opened Windows, you can reset the settings to the default by clicking on the Reset Firefox button
- Mozilla Firefox restart and the settings will be set to the default
Steps to remove malicious extensions from Chrome browsers:
Open the Chrome browser and click on the Chrome menu. In the drop down menu, choose More Tools and then Extensions:
In the Extension Window, look for recently added malicious add-ons and move it to the Trash and any such extensions are located. Note that, you can safely install all the extensions from the Google Chrome browser. However, if you have any problems with the browser redirects and the advertisements –Reset the Google Chrome. Follow these steps in order to reset the browser, disable the extensions and set the default search engine, homepage and startup tabs.
- Open Google Chrome and click on the bars icon at the top right corner of the page
- In the settings page, scroll down to it to find Show Advanced settings
- Search the Reset browser settings option and click on it
- Click on the Reset button on the opened page
- Restart the Google Chrome to changes to take effect
Mac users can download and check if the free scanner can help cleaning OpticalUpdater from their infected system
Protect your Mac from Malware
Mac OS has many features that help you protect the device and the personal information from malicious software or malware. One common way malware is distributed is by embedding it with some regular app. You can reduce this risk using software only from reliable sources. The Security and Privacy settings allow you to specify the sources of the software installed on the device. In addition to this, other types of malware may not be safe. These could be web archives and Java archives. Of course, not all files like this are unsafe, but you should be cautious when opening any such downloaded file. An alert appears when you first try to open them which are an indication of something suspicious. Keeping some antivirus tool installed on the device is also help in achieving system security.
Mac users can download and check if the free scanner can help cleaning DefaultTool ads from their infected system
Remove DefaultTool ads from Mac OS X system
We are going to discussion two possible ways to perform DefaultTool ads removal 1) Manual Removal and 2) Automatic Removal method. The Manual process is more suited to the people who know their system really well. This method is quite unreliable, takes lots of time and need technical skills. Any mistakes during the process can cause major damage to your system. If you cannot reverse such damages, use Automatic Removal Method. It is easy to detect and remove any malicious programs like DefaultTool ads from the device using some reputable antivirus tools like Combo Cleaner. Such tools also offer other important tools like duplicate files finder, clean junk files, huge file finder, privacy protection, browser cleaning and Mac speed booster. For the convenience, we are here providing you both the manual and automatic instruction one by one.
How to remove DefaultTool ads manually?
- First of all, open the Utilities folder on your Mac
- Search for the option Activity Monitor and double-click on it
- Select malicious or suspicious processes related to the DefaultTool ads and click on the cross button from the upper left side corner to end the task
- When a pop-up dialogue box appears on the screen, click on the Force Quit button
The DefaultTool ads can keep coming back on the device if the core files are not completely removed. We recommend you downloading Combo Cleaner. Using this, you can remove all the hidden files and also save time and effort as well.
Automatically remove DefaultTool ads from the Mac OS X
- Click on the link to download Combo Cleaner Antivirus on your Mac
- Drag the install file to Applications folder to install the program
- Go to Antivirus tab, Select Scan Mode and press Start Scan button
- Software will find all the files. You just click on the Remove all the threats button
Remove DefaultTool ads from Applications
- Click Go button at the top left of the screen and select Applications
- Wait till the Applications folder appears, and look for DefaultTool ads or other suspicious programs on it and then right click on each entry and select Move to Trash
Remove DefaultTool ads related files and folders
Click the Finder icon (from menu bar), choose Go and select Go to Folder
Step 1:Check the malware generated files in the Library/LaunchAgents folder
In the Go to folder…. bar, type /Library/LaunchAgents
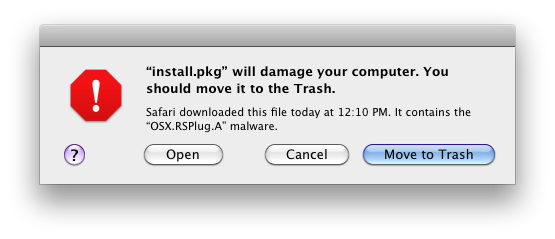
Open the Safari main menu and Choose Preferences from the drop down menu
Go to the Extension tab, and turn off the extension slider to disable all the installed extensions in the Safari browser.
Next step is to check the homepage. Go to the preferences option and choose General tab. Change the homepage option to the default one
If the search engine also got changed, you can set default or other web searcher according to your choice. For this, go to the preferences window and select the 'Search' tab and select the search engine provider that you want to
Next thing you need to do is to clear the browser Cache. For this, go to the preferences window and select the 'Advanced' tab and click on the show develop menu in the menu bar
Then, Select Empty Caches from the Develop menu
Thereafter, remove the website data and the browsing history. Go to Safari menu and select Clear History and Website Data. Choose all history and then click on Clear History.
Guides on removing malicious plug-ins from Mozilla Firefox:
Open the Mozilla Firefox, Click on the Menu at the right top corner of the screen. From the opened menu, choose Add-ons
Best Free Mac Malware Removal
Choose the Extension tab for the recently added suspicious add-ons, if located -click the Remove button next to them. You can safely uninstall all the extensions, however, if you find any trouble, we recommend you Reset the Mozilla Firefox.
- Open the Mozilla Firefox and click on the Firefox button (at the top left corner of the main window)
- In this menu, look for Help sub-menu and select Troubleshooting information
- In this information page, click on the Reset Firefox button
- On the opened Windows, you can reset the settings to the default by clicking on the Reset Firefox button
- Mozilla Firefox restart and the settings will be set to the default
Steps to remove malicious extensions from Chrome browsers:
Open the Chrome browser and click on the Chrome menu. In the drop down menu, choose More Tools and then Extensions:
In the Extension Window, look for recently added malicious add-ons and move it to the Trash and any such extensions are located. Note that, you can safely install all the extensions from the Google Chrome browser. However, if you have any problems with the browser redirects and the advertisements –Reset the Google Chrome. Follow these steps in order to reset the browser, disable the extensions and set the default search engine, homepage and startup tabs.
- Open Google Chrome and click on the bars icon at the top right corner of the page
- In the settings page, scroll down to it to find Show Advanced settings
- Search the Reset browser settings option and click on it
- Click on the Reset button on the opened page
- Restart the Google Chrome to changes to take effect
Mac users can download and check if the free scanner can help cleaning OpticalUpdater from their infected system
Protect your Mac from Malware
Mac OS has many features that help you protect the device and the personal information from malicious software or malware. One common way malware is distributed is by embedding it with some regular app. You can reduce this risk using software only from reliable sources. The Security and Privacy settings allow you to specify the sources of the software installed on the device. In addition to this, other types of malware may not be safe. These could be web archives and Java archives. Of course, not all files like this are unsafe, but you should be cautious when opening any such downloaded file. An alert appears when you first try to open them which are an indication of something suspicious. Keeping some antivirus tool installed on the device is also help in achieving system security.
Mac users can download and check if the free scanner can help cleaning DefaultTool ads from their infected system
Remove DefaultTool ads from Mac OS X system
We are going to discussion two possible ways to perform DefaultTool ads removal 1) Manual Removal and 2) Automatic Removal method. The Manual process is more suited to the people who know their system really well. This method is quite unreliable, takes lots of time and need technical skills. Any mistakes during the process can cause major damage to your system. If you cannot reverse such damages, use Automatic Removal Method. It is easy to detect and remove any malicious programs like DefaultTool ads from the device using some reputable antivirus tools like Combo Cleaner. Such tools also offer other important tools like duplicate files finder, clean junk files, huge file finder, privacy protection, browser cleaning and Mac speed booster. For the convenience, we are here providing you both the manual and automatic instruction one by one.
How to remove DefaultTool ads manually?
- First of all, open the Utilities folder on your Mac
- Search for the option Activity Monitor and double-click on it
- Select malicious or suspicious processes related to the DefaultTool ads and click on the cross button from the upper left side corner to end the task
- When a pop-up dialogue box appears on the screen, click on the Force Quit button
The DefaultTool ads can keep coming back on the device if the core files are not completely removed. We recommend you downloading Combo Cleaner. Using this, you can remove all the hidden files and also save time and effort as well.
Automatically remove DefaultTool ads from the Mac OS X
- Click on the link to download Combo Cleaner Antivirus on your Mac
- Drag the install file to Applications folder to install the program
- Go to Antivirus tab, Select Scan Mode and press Start Scan button
- Software will find all the files. You just click on the Remove all the threats button
Remove DefaultTool ads from Applications
- Click Go button at the top left of the screen and select Applications
- Wait till the Applications folder appears, and look for DefaultTool ads or other suspicious programs on it and then right click on each entry and select Move to Trash
Remove DefaultTool ads related files and folders
Click the Finder icon (from menu bar), choose Go and select Go to Folder
Step 1:Check the malware generated files in the Library/LaunchAgents folder
In the Go to folder…. bar, type /Library/LaunchAgents
Look for any recently added suspicious files in this folder. Such files could be 'installmac.AppRemoval.plist', 'myppes.download.plist', 'mykotlerino.ltvbit.plist', 'kuklorest.update.plist', etc. If you find any similar, move them to the Trash.
Step 2:Erase the suspicious files from '/Library/Application' Support folder
Type '/Library/Application Support' in this folder
In the Application Support folder, you may find MplayerX or NicePlayer or other similar suspicious folders. Move these folders to the Trash.
Step 3: Check the /Library/LaunchDaemons Folder for the suspicious files created by malware Wt library 2013 for mac.
In the Go to Folder… bar, type /Library/LaunchDaemons
In the LaunchDaemons folder, search for the files 'com.aoudad.net-preferences.plist', 'com.myppes.net-preferences.plist', 'com.kuklorest.net-preferences.plist', 'com.avickUpd.plist', etc and move them to the Trash
Scan Mac For Malware Free
Step 4: Use Combo Cleaner and scan your Mac
After performing all the steps mentioned before in correct manner, your Mac should be cleaned of the infections. However, you must ensure this by running a scan to the power-station with Combo cleaner anti-virus.
After the download, double click the combocleaner.dmg installer in the opened Window drag and drop the antivirus tool icon on the top of the Application icon. Thereafter, open the Launchpad and press on Combo Cleaner icon. The Combo Cleaner then starts update its virus definition database – you should have to wait till the moment till the process is completed. Next thing you do is to click on the Start Combo Scan button.
The anti-malware tool starts scanning your Mac device for malware infections. After the scanning, if it displays no threats found – you can continue with the removal guide, otherwise you have to perform removal of the found infections.
After removing the files and folders generated by the malware, the next thing you do is to remove the rogue extensions installed on the Internet browsers.
Remove DefaultTool ads from Internet browsers
Instruction on removing suspicious Safari extensions:
Open Safari from the menu bar, select Safari and click preferences
In the preferences window, select extensions and search for recently installed suspicious extensions. If any such extensions located, click on uninstall button next to them.
Generally, users can simply remove all these extensions. However, if you have any problems with the browser redirects and the unwanted advertisements, we recommend you 'Reset the Safari'. The reset feature is capable of fixing various issues related to the browser hijackers and adware. Also, the resetting the browser does not mean that the essential information such as bookmarks and open tabs will also be deleted. By using the steps, you will reset the extensions, themes, search engines, security settings, plug-ins settings, toolbar customization, user styles and other settings. Here are the step by step instructions on performing the steps:
Open the Safari main menu and Choose Preferences from the drop down menu
Go to the Extension tab, and turn off the extension slider to disable all the installed extensions in the Safari browser.
Next step is to check the homepage. Go to the preferences option and choose General tab. Change the homepage option to the default one
If the search engine also got changed, you can set default or other web searcher according to your choice. For this, go to the preferences window and select the 'Search' tab and select the search engine provider that you want to
Next thing you need to do is to clear the browser Cache. For this, go to the preferences window and select the 'Advanced' tab and click on the show develop menu in the menu bar
Then, Select Empty Caches from the Develop menu
Thereafter, remove the website data and the browsing history. Go to Safari menu and select Clear History and Website Data. Choose all history and then click on Clear History.
Guides on removing malicious plug-ins from Mozilla Firefox:
Open the Mozilla Firefox, Click on the Menu at the right top corner of the screen. From the opened menu, choose Add-ons
Choose the Extension tab for the recently added suspicious add-ons, if located -click the Remove button next to them. You can safely uninstall all the extensions, however, if you find any trouble, we recommend you Reset the Mozilla Firefox.
- Open the Mozilla Firefox and click on the Firefox button (at the top left corner of the main window)
- In this menu, look for Help sub-menu and select Troubleshooting information
- In this information page, click on the Reset Firefox button
- On the opened Windows, you can reset the settings to the default by clicking on the Reset Firefox button
- Mozilla Firefox restart and the settings will be set to the default
Steps to remove malicious extensions from Chrome browsers:
Open the Chrome browser and click on the Chrome menu. In the drop down menu, choose More Tools and then Extensions:
In the Extension Window, look for recently added malicious add-ons and move it to the Trash and any such extensions are located. Note that, you can safely install all the extensions from the Google Chrome browser. However, if you have any problems with the browser redirects and the advertisements –Reset the Google Chrome. Follow these steps in order to reset the browser, disable the extensions and set the default search engine, homepage and startup tabs.
- Open Google Chrome and click on the bars icon at the top right corner of the page
- In the settings page, scroll down to it to find Show Advanced settings
- Search the Reset browser settings option and click on it
- Click on the Reset button on the opened page
- Restart the Google Chrome to changes to take effect
Mac users can download and check if the free scanner can help cleaning DefaultTool ads from their infected system
Protect your Mac from Malware
Mac OS has many features that help you protect the device and the personal information from malicious software or malware. One common way malware is distributed is by embedding it with some regular app. You can reduce this risk using software only from reliable sources. The Security and Privacy settings allow you to specify the sources of the software installed on the device. In addition to this, other types of malware may not be safe. These could be web archives and Java archives. Of course, not all files like this are unsafe, but you should be cautious when opening any such downloaded file. An alert appears when you first try to open them which are an indication of something suspicious. Keeping some antivirus tool installed on the device is also help in achieving system security.

